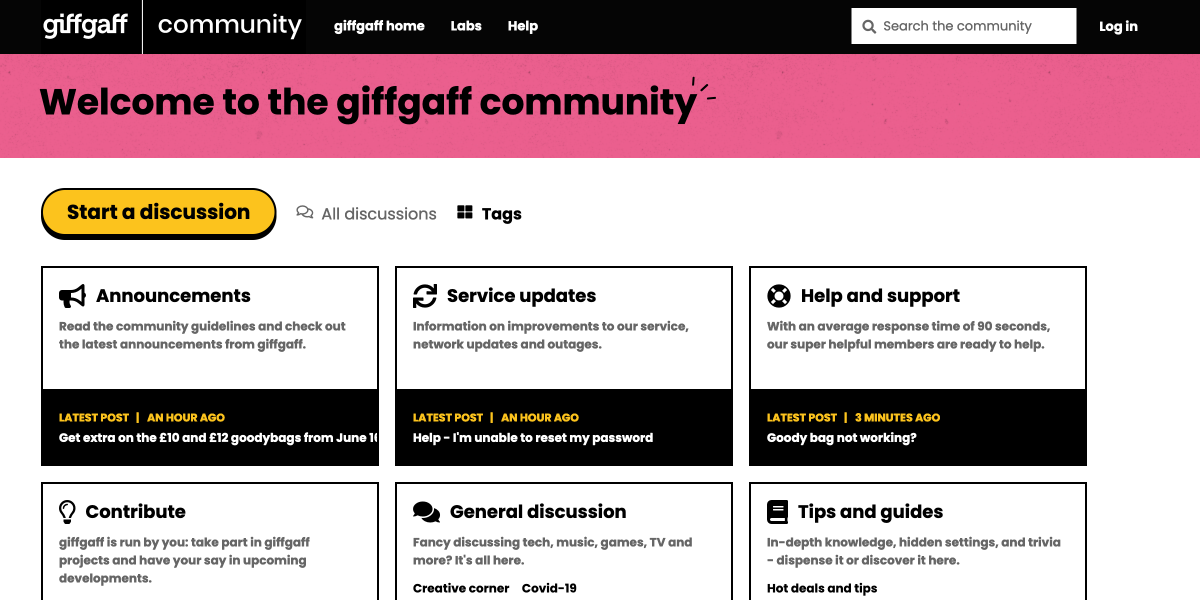
As a leading British telephone network, giffgaff serves millions of customers. Through innovative use of Flarum, they've built up a passionate peer support community, improving support and engaging customers.

As a leading British telephone network, giffgaff serves millions of customers. Through innovative use of Flarum, they've built up a passionate peer support community, improving support and engaging customers.
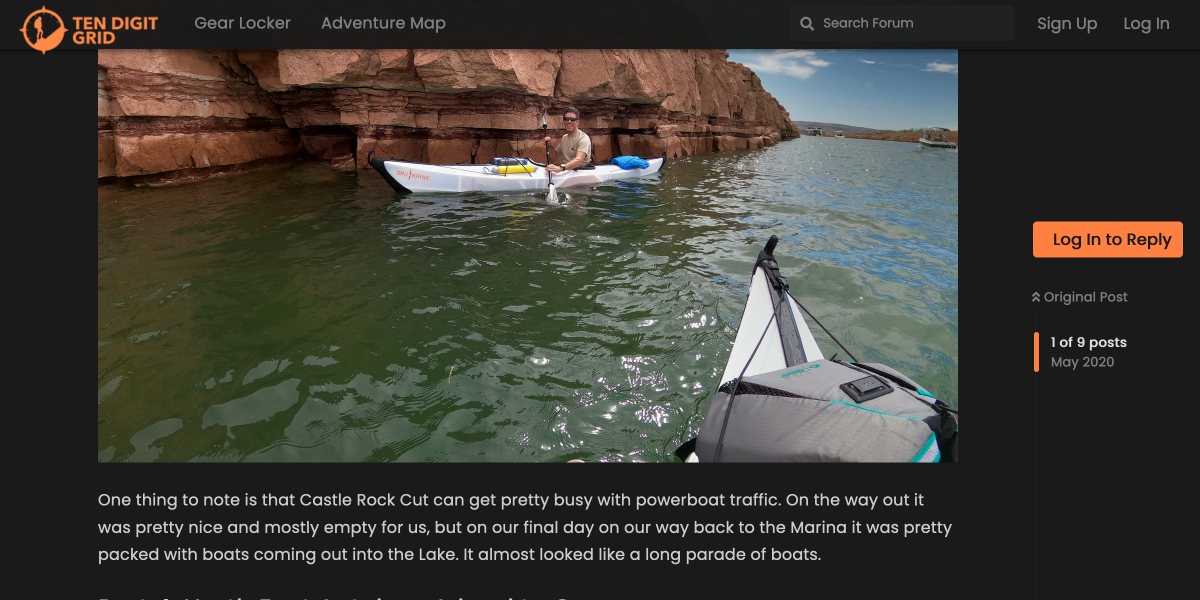
An avid adventurer and hiker, Mike has found Flarum to be an excellent platform for blogging about his trips, discussing gear, and meeting fellow hiking enthusiasts while slowly increasing engagement.
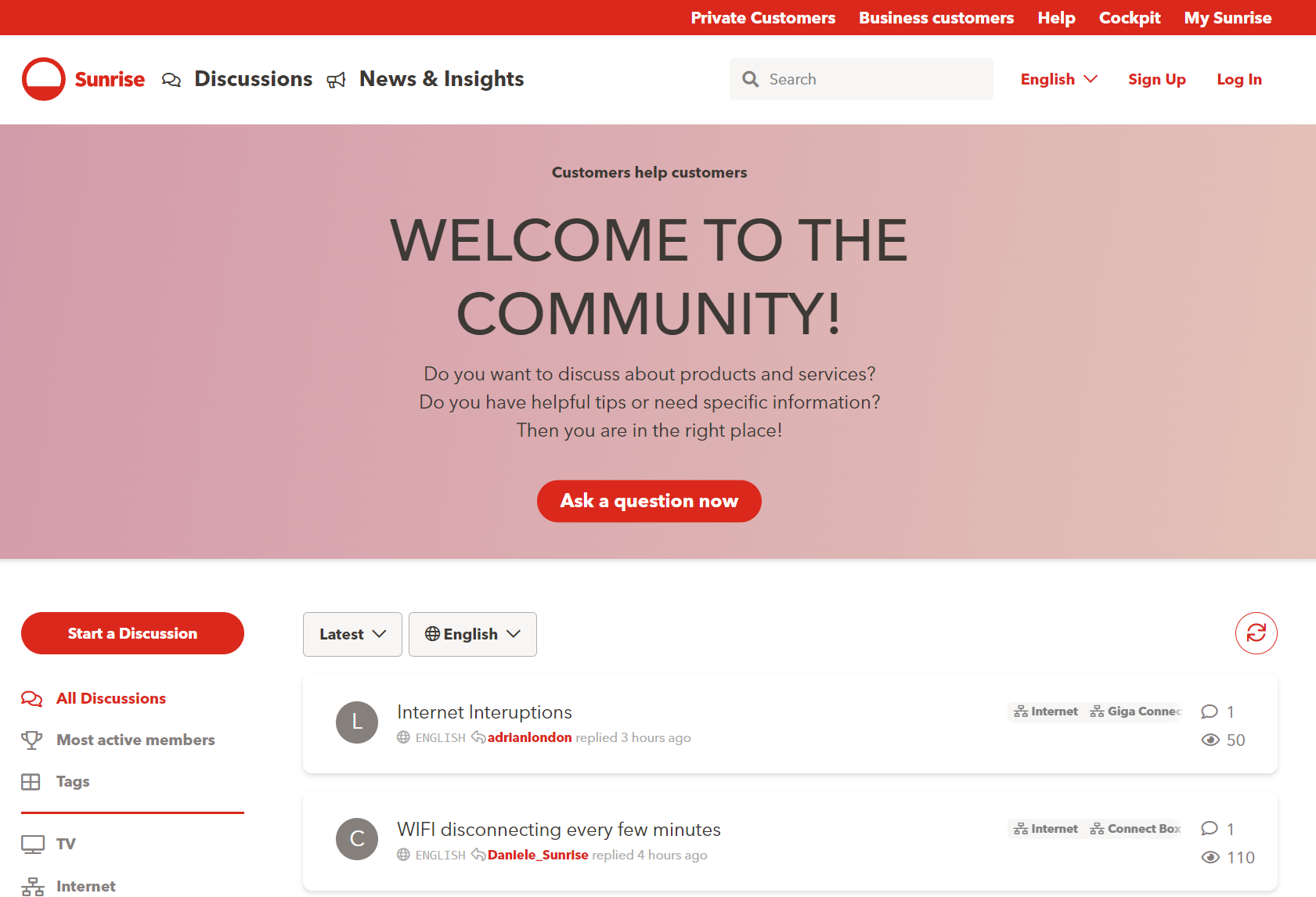
Leading provider of communication and entertainment in Switzerland. Their Flarum community creates a framework for healthy togetherness while supporting their customers with an appealing, user-friendly community experience.
Learn how to harness the extensibility of Flarum to create your own extensions and customize your community.
Help us make Flarum even more powerful and customizable! Every bug report, pull request, and documentation improvement is a huge help.