Modern, fast & free community software
The community framework for small to enterprise communities that is extensible, scalable and completely free!
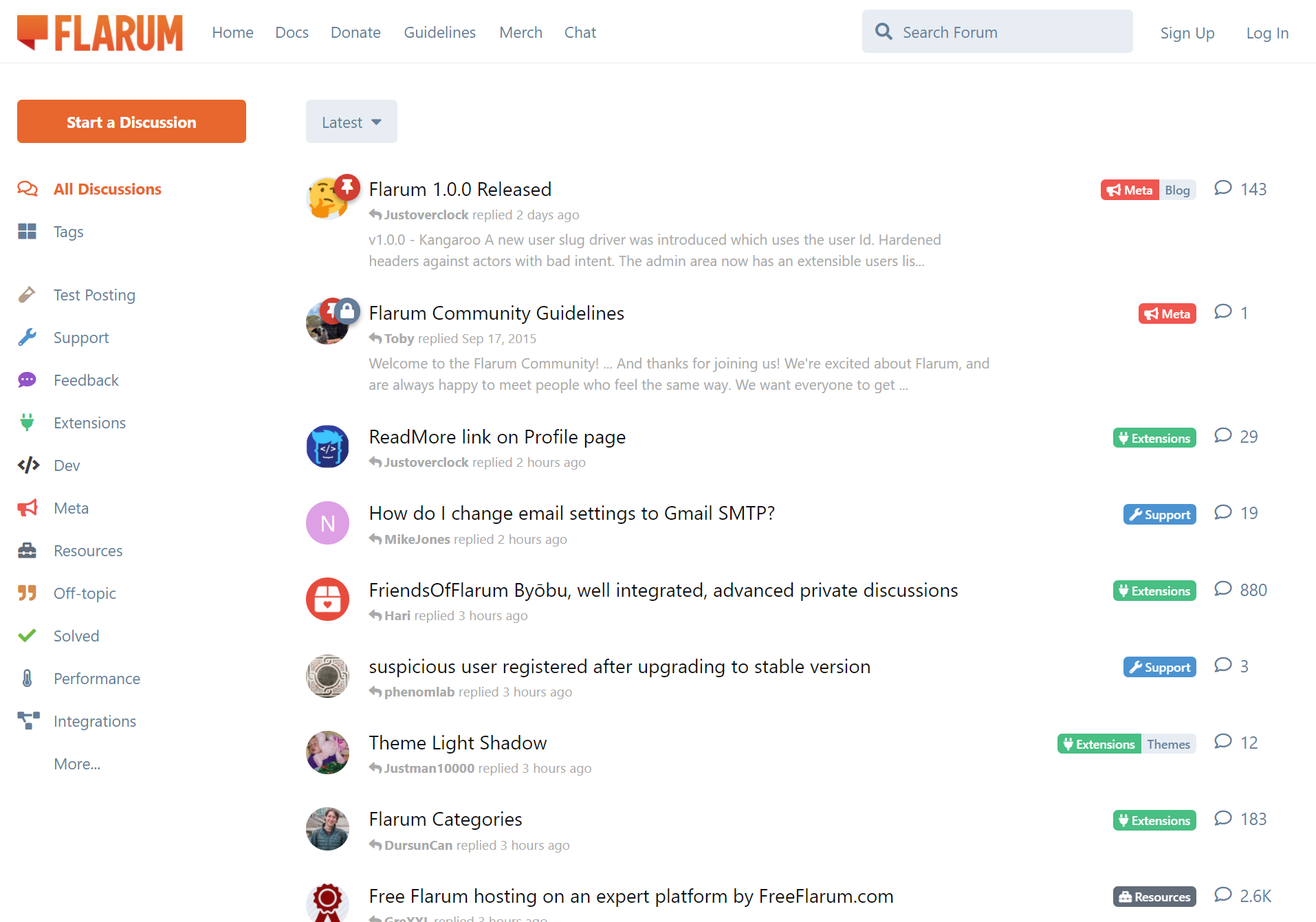
The community framework for small to enterprise communities that is extensible, scalable and completely free!

Community platform
Regardless of the size of your community, Flarum excels on every level. Building on top of the Flarum core experience with extensions allows you to customize your community to your needs.
Groups and permissions
Powerful editor
Styling and themes
Notify and engage
Extend endlessly

Flarum is open source so that anyone can install it anywhere, even on a shared hosting plan. No vendor lock-in, you own your data, no hidden fees!

A helpdesk system
Create your own helpdesk on top of Flarum. Self service articles and staff ticket lists are all included.

Paid membership community
Engage with your audience on this friendly and welcoming platform where you are in full control! Increase recurring revenue from increasing subscriptions and grow into sustainability.

A web3 community
A decentralized community powering innovative, groundbreaking web3 projects starts with software that allows you to shape it anyway you need.